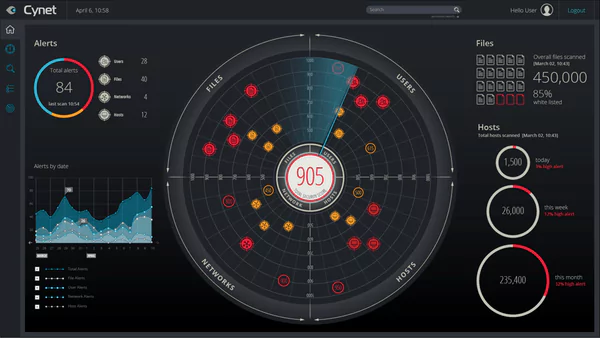
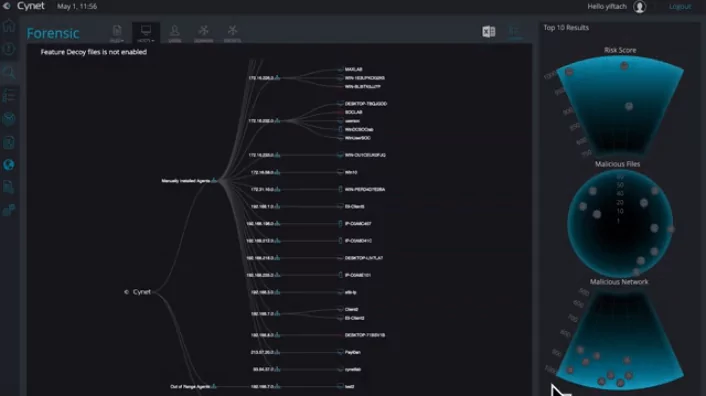
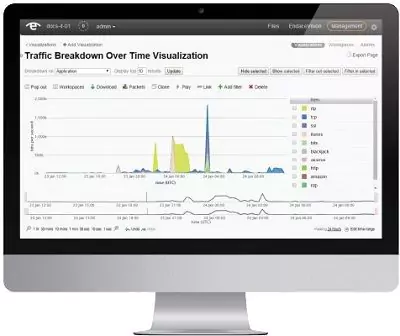
Continuous validation of your security with Breach and Attack Simulation (BAS)

Undoubtedly, you have the security of your ICT systems in order. Various tools protect your network against possible intruders.
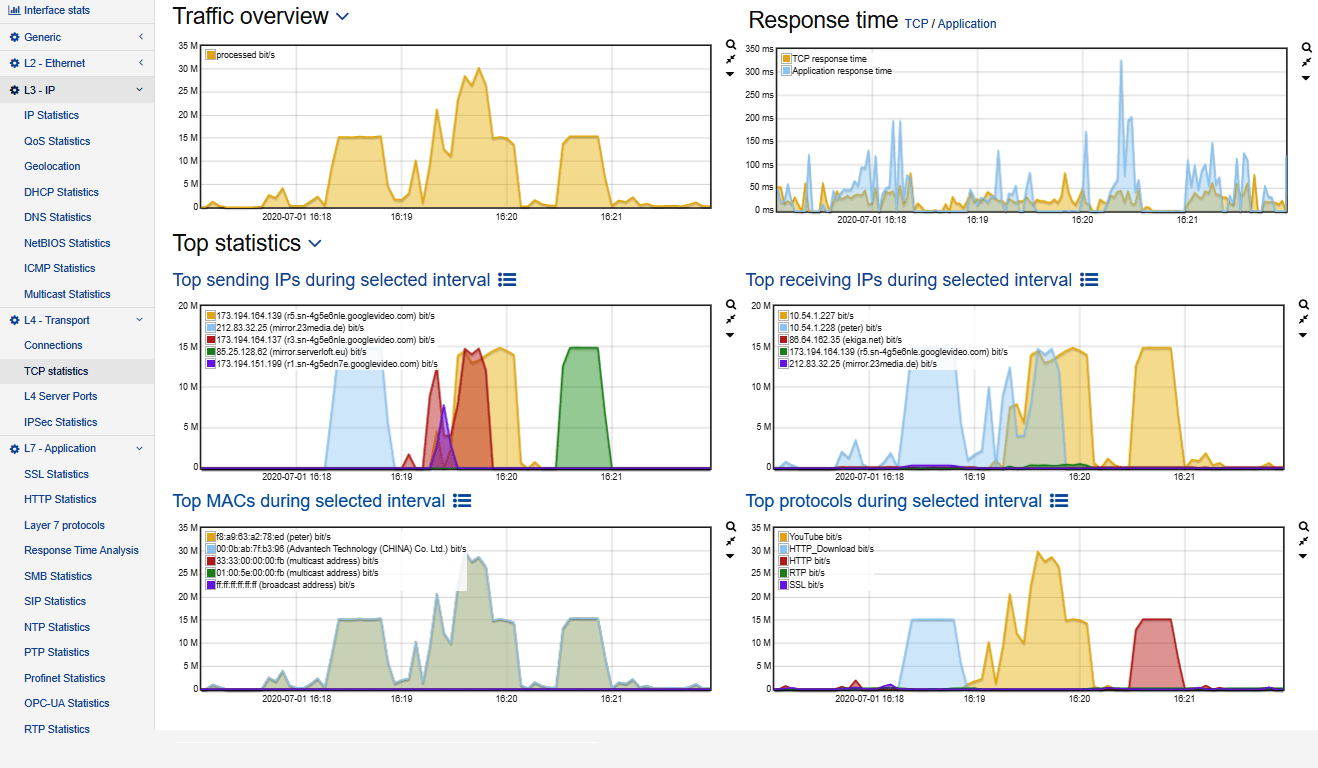
However, your ICT environment is constantly changing, for example through patches and updates. How can you be sure that your network, applications and data are just as secure as when your tools were originally implemented?
Also, security certification often obliges you to continuously validate your ICT security.
What do we offer?
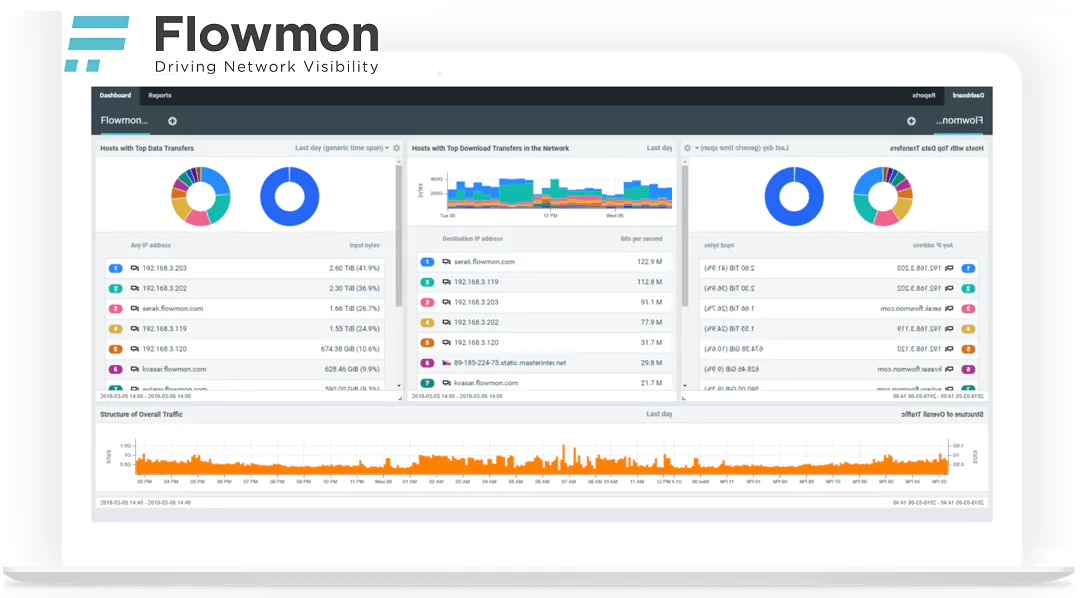
We offer Security as a Service (SaaS). A combination of an advanced software solution and services with which we de-stress you completely.
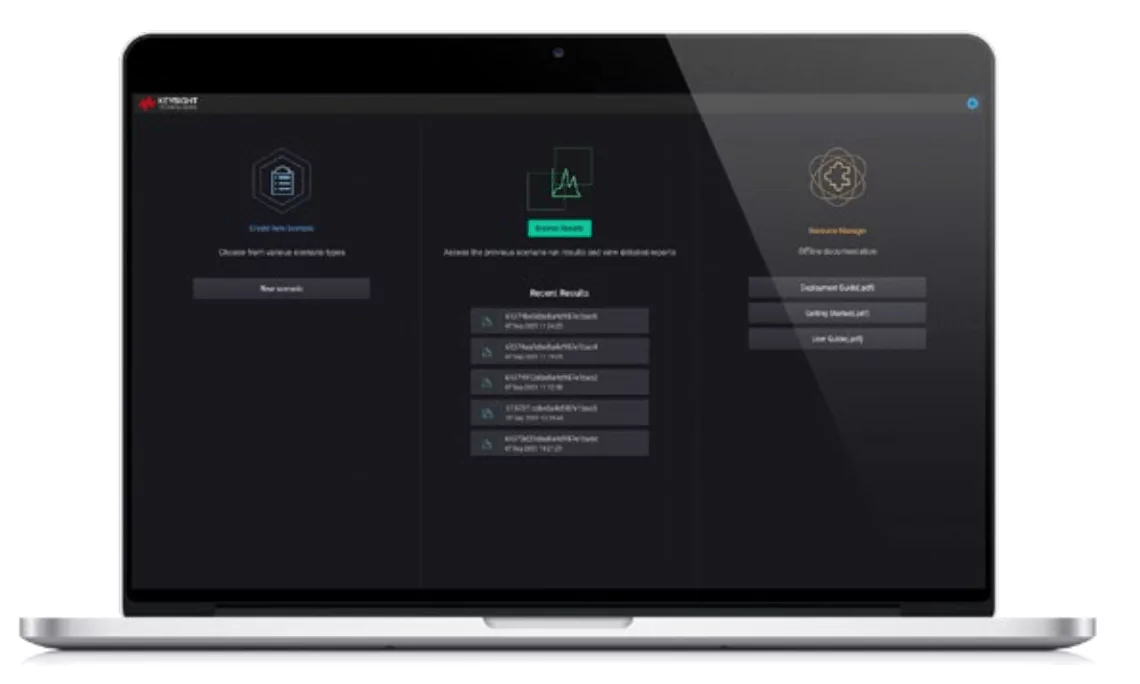
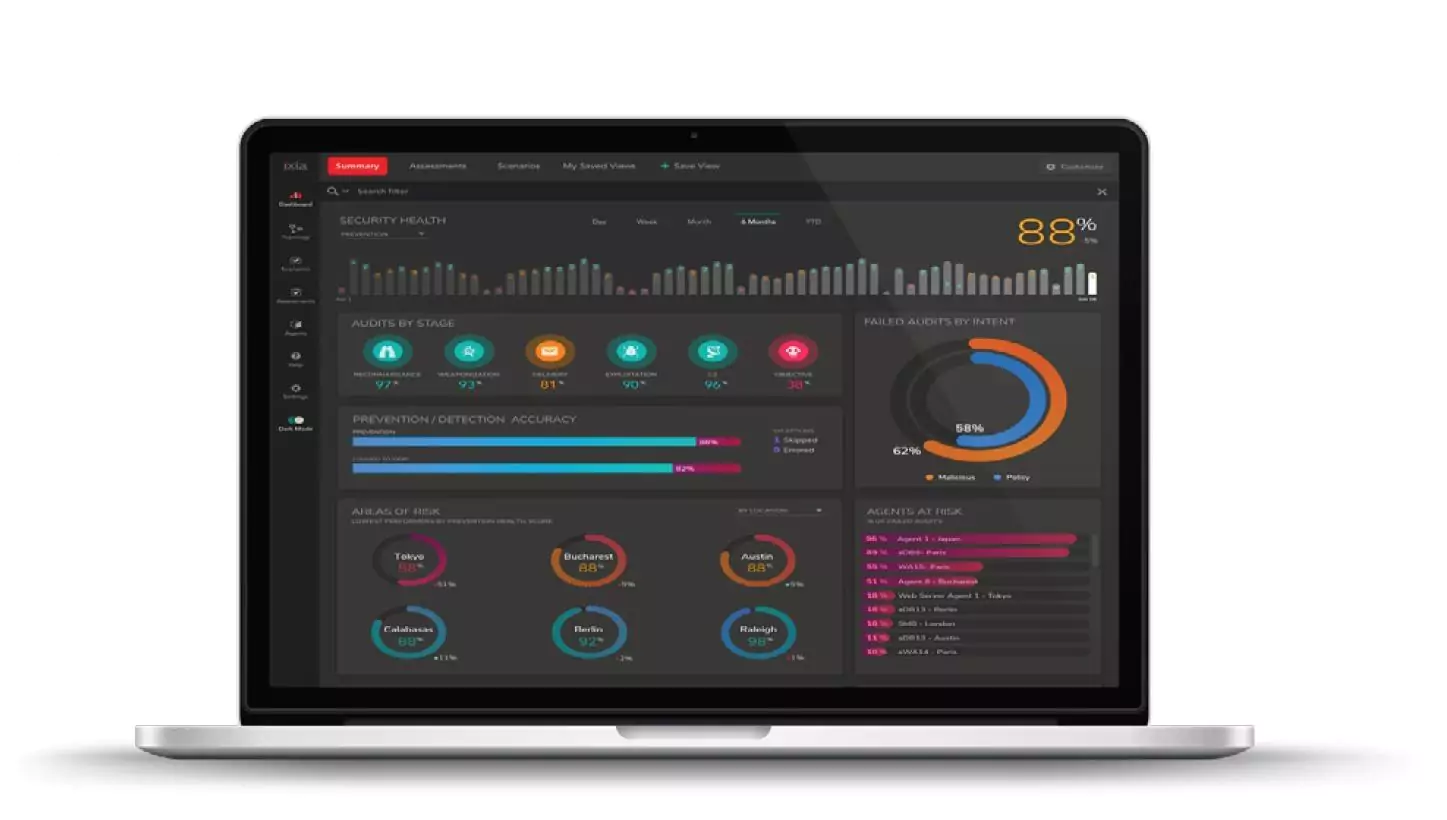
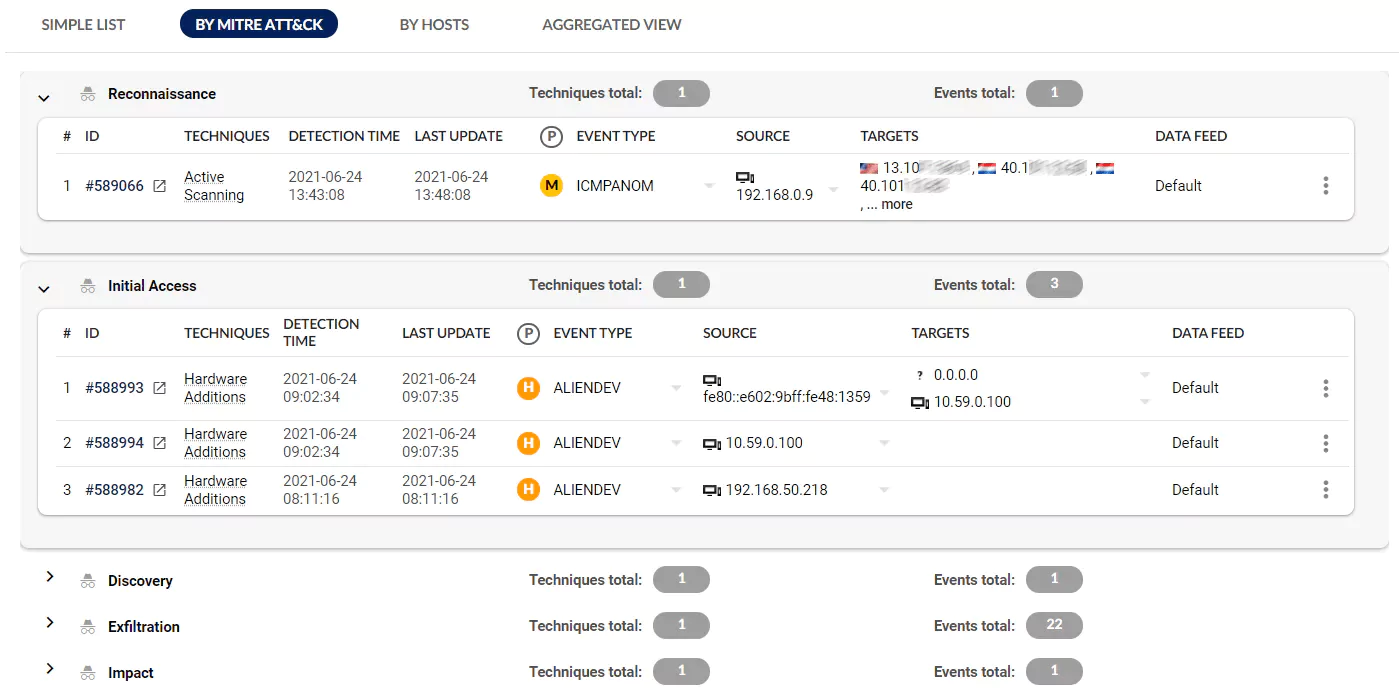
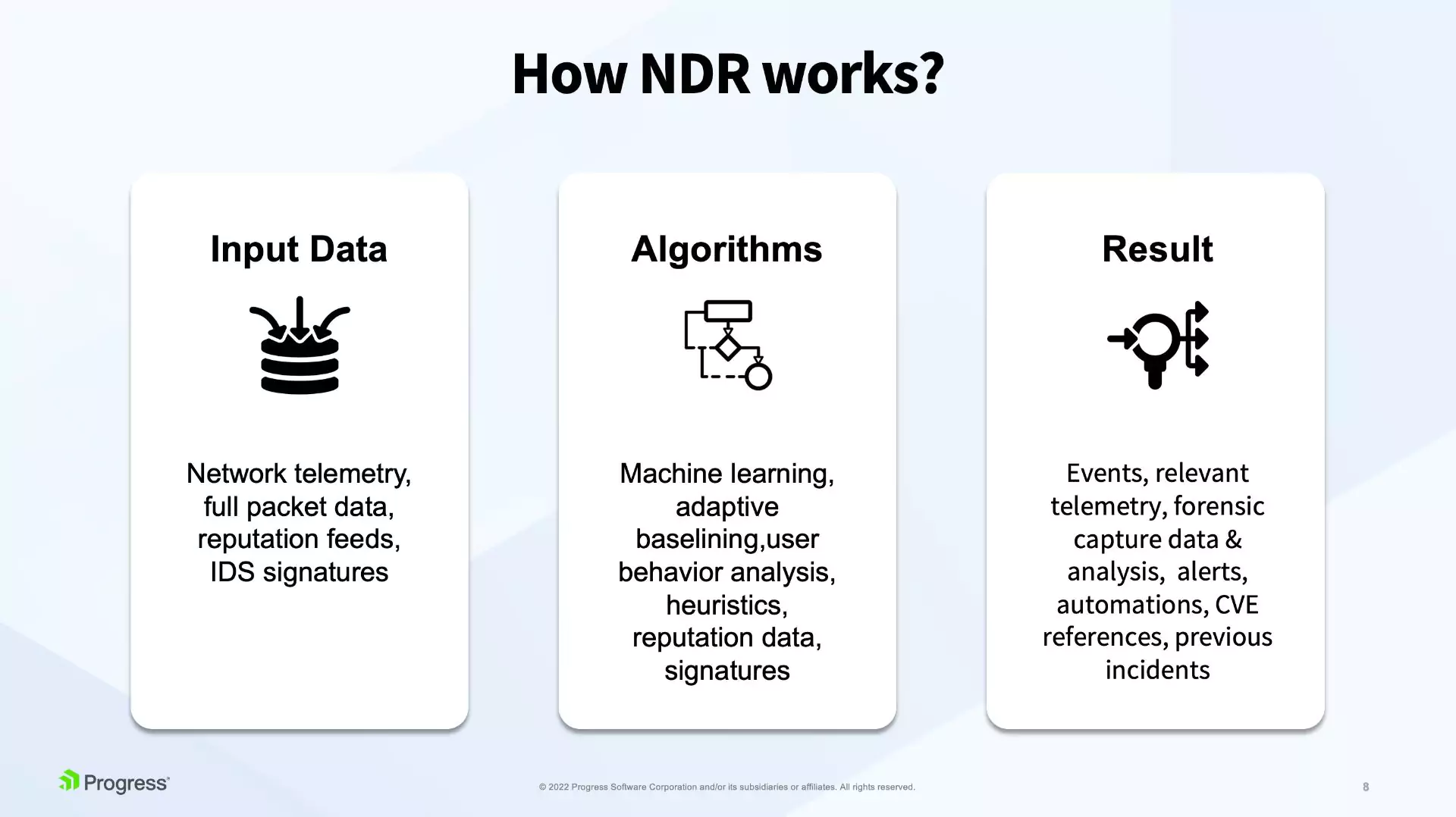
Our Breach and Attack Simulation tools offer a safe way to test your security. Possible vulnerabilities are detected before intruders do. We use Keysights Threat Simulator, which is based on the MITRE ATT&CK framework. Software agents use known exploits and techniques to see if your ICT environment is secure.
Think of it as a practice session for your security tools so you can evaluate their effectiveness, address weaknesses and optimize your tactics for optimal security.
We can configure this software for your environment, create reports and make recommendations to improve your security. By doing so, the evaluation hardly takes any effort on your part.
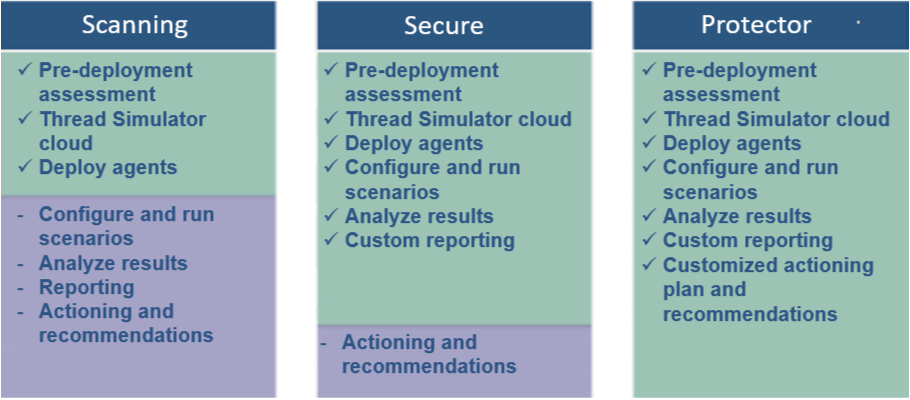
What is the pricing?
The costs depend on the requested service level and the number of agents needed.
How many agents you need depends on your ICT environment and requirements.
We offer three service levels which are described above.
Scanning support starting at € 4,250 per year
Secure support starting at € 6,800 per year
Protector support starting at € 12,000 per year
Protect your organisation today!
Contact one of our experts for an exact quote. Together, we can make sure your systems are protected from the ever-changing threats of the digital landscape.